What is the Deep Web? and How To Access It

Image from Genee Research
**WARNING** The deep Web is not for the faint of heart.
The deep Web is technically classified as websites that the public doesnâ??t have access to. The way most people find desired information is by using a search engine. If a website cannot be found through a search engine then we can say that it is part of the deep Web; because the information is buried deep within the internet. Anything that is accessible publicly through search engines is referred to as the surface Web.
So what is so awesome about this hidden Web? Well for starters the deep Web offers over 7,500 terabytes of information while the surface Web offers a mere 19 terabytes [1]. The surface Web has only 1 billion individual documents whereas the deep Web has over 550 billion.The deep Web content quality is also at least 1,000 to 2,000 times better than the surface Web.
Although websites that are in the deep Web cannot be found by search engines, there is another way to access them.
Enter Tor
Tor is a system that was first funded by the US Navy to protect government communications. Tor makes it hard to trace someoneâ??s online activity by encrypting data and sending it through random routes. This system was so effective that eventually people started using it for many different reasons.
People that lived in countries that censored their internet could now access anything without fear of being tracked. Individuals could use Tor to keep their identity and browsing history private. With Tor, civil liberties can be protected online and freedom of speech can be expressed by people in countries where they would be normally oppressed.
Tor is a virtual network hidden within the internet. Websites hosted on Tor use .onion domains. You cannot access these websites without using the Tor gateway and becoming part of this system. For that reason search engines cannot index the deep Web. This makes Tor the ultimate outlet for sensitive information because everything is off the record.
So naturally this network will attract a lot of legitimate users as well as illegitimate users. Because the Tor network is open and anonymous there is information there that attracts hackers, assassins, scientists, inventors, activists, government officials, police, and more. It may seem as if the deep Web is malicious when it really is just an open network. As with the surface Web you cannot really control who uses the internet and what they use it for.
The deep Web at this level is like a hidden library. There is no search engine for finding information although there is a detailed directory of the websites hosted on Tor. These websites can include anything from scientific research to online drug stores.
If you are looking for unreleased scientific information or the works of deceased inventors, this is the place to find it. If you are looking for first hand accounts of living in North Korea and other communist countries, this is the place you would come to research. There’s blogs, forums, and directories scattered across the deep Web that cover any imaginable topics.
Whistleblower’s Haven
The deep Web is also a place where whistleblowers publish their leaks. Since the whole network is anonymous it is easy for people to leak information and news. While people may publish leaked documents alleging government and corporate misconduct, it is important to note that it is also easy to fake leaks. The reputation of people who release leaks is based on whether their predictions become true, or their past leaks have been confirmed by officials. At any rate it is quite hard to discern truth from fact since anyone can “leak” information. I personally wouldn’t trust these leaks seeing that a company can provide “leaks” of their competitors.
A public website named Wikileaks was created in 2006 which would publish all these allegations from within the deep Web. An example of the information that was published in the deep Web is 779 secret files on the prisoners detained in Guantanamo Bay.
Wikileaks isn’t protected by the same anonymous safety net that the deep Web is. Much controversy and charges surround the entire website. As of today 8/8/2012 Wikileaks is down.
Accessing The Deep Web
To access the deep web you will need to download Tor. Afterwards extract the file that you downloaded and open the extracted folder called Tor Browser. In that folder there will be an application that is named Start Tor Browser, open it.
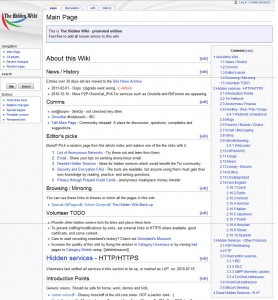
It will take a while for the program to setup random anonymous routes for your traffic. When Tor is finished loading, a custom Firefox browser will open up, in which you can navigate to kpvz7ki2v5agwt35.onion. Just enter that link in your address bar and wait a few minutes at most. This link takes you to something called “The Hidden Wiki” which is the most known directory of the deep Web.
If you don’t want to try exploring the deep Web yourself, you can click on the image below to see how the Hidden Wiki looks.
Other Uses of Tor
You can also access normal websites using Tor. When you do this your IP address will be completely masked. There are even operating systems out there such as Tails, that encrypt and Torify all of your applications data.
One thing to watch out for is that there is a vulnerability to Tor. All of your data has to be decrypted at a Tor exit node and then sent to the server address you are trying to access. Whoever has control over this exit node will be able to see all of your data. So to be 100% anonymous you must use a VPN and Tor. You can learn more about how Tor functions at their website.
Usefulness
Although the usefulness of the deep Web can be debated, one thing is for sure. Any information you seek, can most likely be found in the deep Web.
The deep Web may have malicious information. This website does not condone or promote illegal activities.  Although there are many practical uses for the deep Web, it is important not to get involved in harmful activities. The deep Web is like a city, and any harmful information is like a dark alley. Your best bet is to not wander around and get yourself in trouble. If you see something on the hidden web that looks fake, such as a hitman network, do not be tempted to check these things out! Nine chances out of ten you will actually find yourself on a hitman network!
I can attest to this software being useful in countries where your ISP may censor your internet. Recently I had a friend that was visiting a country, and his ISP was blocking Youtube, Facebook, and other websites. Guess what I recommended to him?
The Economy of The Deep Web
The deep Web has its own currency called Bitcoins. Bitcoins is a cryptocurrency that is decentralized and serves as anonymous electronic cash. Naturally this payment type would appeal to most criminals, and sadly that is what it is mostly used for. The fact that someone can pay hitmen and buy guns through an anonymous deep Web with an anonymous currency kind of freaks me out. Luckily police and internet vigilantes often try to take down illegal websites.
1. The information given about the size of the web is based on a study from 2001. Although this study may be seen as “outdated”, it still serves the purpose of understanding how much bigger the deep Web is when compared to the surface Web.
Article written by Octavian Ristea.


These are some of the best articles i have ever read. Octavian helped me decide to build a cpu and really informed me about some really cool and diverse topics. I really give you props bud and keep up the good work.
Haha, this is my friend that I recommended Tor to. Thanks man.
Awsome! What a shocking ratio of content vs. the normal Web. It’s like a kind of underground web city, sitting right underneath us the whole time. I’ve been messing about with websites for 4 years now and I admit that I’d never even heard of The Deep Web, let alone how to access it lol It’s like being given a pass key to a brand new adventure via the Web. Anyone adventuring within the Deep Web, let us know what you find . . .
:Cool:
Woa . . . just clicked on and magnified the first page of ‘Hidden Wiki’ that’s in the article. There are some interesting areas and some dark areas. The warning Octavian gave is understandable as there is even an ‘Assassinations Market’!
Maybe here you can shop around and add sniper assassinations or melee attack assassinations to your basket. 20% discount on head shots. Buy now! (Just kidding . . . but not about the ‘Assassinatons Market’ – magnify the first Hidden Wiki page and you’ll see)
I’m making an amateur movie and this would be great to include in the storyline. I wonder if I could put the process of accessing the Deep Web in the movie, or maybe the software is copyrighted so I can’t show it?
Yeah that’s the hard part about joking about this stuff. People will think the whole thing is a hoax and they will turn a little sick when they realize the guys on there are for real. Those spy networks you see in movies? Tor network. :Pleasure:
So I am glad I included the warnings and image preview.
As for your question about copyright problems; you literally made me laugh out loud. From what I understand Tor is open source. By the people for the people. Don’t take my word for it… But I am sure they will enjoy the exposure. Tor will become accessible to more people that way.
At which point one has to ask himself: how exactly does this fit into your movie?
Yes, the copyright question was funny now I think about it 😉 lol
This may fit in with the movie as there are people after the main character for a debt owed by his dead brother, which he couldn’t pay. He could somehow hire a computer crime expert to track down the source of who ordered the hit . . . or even some kind of cover up, or something like that anyway 😉 I’d have to give it some thought though. I wouldn’t want it to be another corny CIA cover up type storyline. If I watch one more movie where the CIA pops up I think I’ll collapse in a severe state of boredom as it’s so hackneyed now.
I’ve turned a few movies off where the old chestnut “Oh my God, it was a CIA cover up all along!” type line comes up. I can’t handle it anymore, it’s gotten as corny as pie throwing was in silent movies now :0
Scrap that idea. Too corny. I think a document buried in the Deep Web with a warning message would be more original 🙂
This must be a sign of madness as I’m replying to myself now :Distort:
That sounds awesome! Tor is in fact open source. This is the link to their creative commons http://creativecommons.org/licenses/by/3.0/us/ From what I understand you are just shooting a movie and not copying or distributing the work (Tor). As for attribution, I guess just saying Tor in the movie would cover it.
If the document is buried in the deep web and is at the same level of importance as the CIA, then it would probably be utilizing PGP http://en.wikipedia.org/wiki/Pretty_Good_Privacy . PGP The only way for him to decode the message would be if he had the decryption key (maybe he found it somewhere else in real life, or he also found the key on Tor.) Most viewers won’t know what the heck PGP is, but hopefully they will know what encryption is. Just something you can base it off of if you do end up going that route 😛
Haha I found this awesome graphic http://brandpowder.files.wordpress.com/2011/10/deep-web.jpg
Explains it better than my article 🙂
Liked the graphic 🙂 Thank you Octavian for your suggestion on PGP and how an encryption key would be needed. I really like this idea. I’m going to run with this. This gives me a flood of ideas now. Thank you 🙂
The way you format your posts has changed the way I post articles that I will write personally from now on. Before I would just put a single graphic above the H1 text. Now I’ll change to adding interesting links, more pictures and sometimes a video from now on.
I’m writing a post (when I have snippets of free time) at the moment titled ‘Are You In Control Of Your Mind?’ and will apply this new format that I’ve learned from you Octavian.
The posts just seem more interesting and come alive more with your improved format.
If you surf the web looking for advice on blogging etc. Most of the advice seems SEO-centric, which is fine but it’s not taking into account the reader’s feel good factor when reading the post. Most bloggers put pictures and videos at the bottom of the priority list as it not that effective when it comes to SEO. I think however, who cares . . . I’d rather post articles that are rich in content and pleasing to read, rather than a bombardment of text only type mediocre posts.
Guest posts I don’t have much control over as I don’t like to change people’s articles in any way if I can help it, although most guest posters will include images. Some guest posts are outstanding too. But from now on, articles that I will write personally I will keep to this new and improved format that you have shown me.
Funny I tried to mimic your style 🙂 Glad we can both learn from each other.
I honestly thought whatever I was posting was a little dubious… That’s why I was trying to “fit in”, ahahahahaha.
As for the content and images, it reminds me of how I would describe myself “I am an English speaker, own a small web design company, love technology, understand SEO topics, and niche websites. I also understand the importance of great content, that fuels social media, not just the search engines.”
The last part is the part that is important 🙂 Search engines might bring visitors but doesn’t mean your content won’t drive them away…
( http://www.youtube.com/watch?v=8To-6VIJZRE The bottom will make sense…)
Conversion rates
Bounce rates
Conversion rates
Bounce rates
Conversion rate
Bounce rates
Conversion rates
Bounce rates
So yeah I enjoy images and great content, you can see how my old website used to look 😀 http://laetadesigns.com/wp-content/gallery/htbat/4-27-2012-6-56-51-pm.png
http://laetadesigns.com/wp-content/gallery/htbat/4-27-2012-7-01-52-pm.png
(Bummer I don’t have an image of an actual post. Anyways they used to look great. I only used 600×200 images to get this awesome effect.) I like using eye candy.
As for the “format” I’ve shown you, like I said its just what came out of my style trying to mix in with yours. That’s the best part about it 😀
I haven’t gotten to writing posts, but I’ll get back to it. Its been a few days yet I already miss it 🙂